What is network segmentation?
Network segmentation is a network architecture approach that divides a network into multiple segments often referred to as subnets, each acting as its own smaller network. This allows administrators or owners to control the flow of traffic between these subnets based on policies. Organizations use segmentation to improve monitoring, boost performance, localize technical issues, and most importantly, enhance security. For a long time, segmentation has been used in enterprise and even small businesses to limit the reach of anyone device that is connected to the large network.
English, please?
Let’s say that you go to Starbucks and connect to their Wi-Fi, if you had a scanning device and started to scan the network for other devices, you shouldn’t be able to see Starbucks point on sales devices in your scan even though those devices may also be connected using Wi-Fi.
A network works a lot like other methods of communication in the sense that it is based on addresses. Your internet provider gives you an address that you will use when making requests to the internet, when doing things like browsing, checking email, reading blog articles, etc. Those destinations also have an address. There is a quick and easy way to check those addresses, you can simply open a terminal or command prompt on your machine and type “ping google.com”, or any other website of your choice.
You should get a response that looks like the capture below…
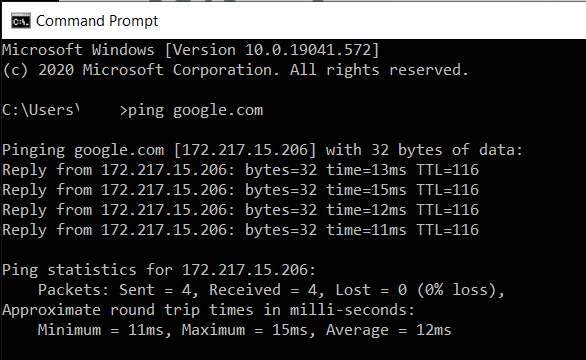
What does any of that have to do with network segmentation?
Now that we know about the concept of addresses, let’s look at what happens to devices when they are connected to our home network. Most people will have at home either a Modem/Router/Wi-Fi device from the Internet provider, or some will get their modem, router, and in some cases dedicated access points for Wi-Fi.
Here is a diagram of what that can look like…
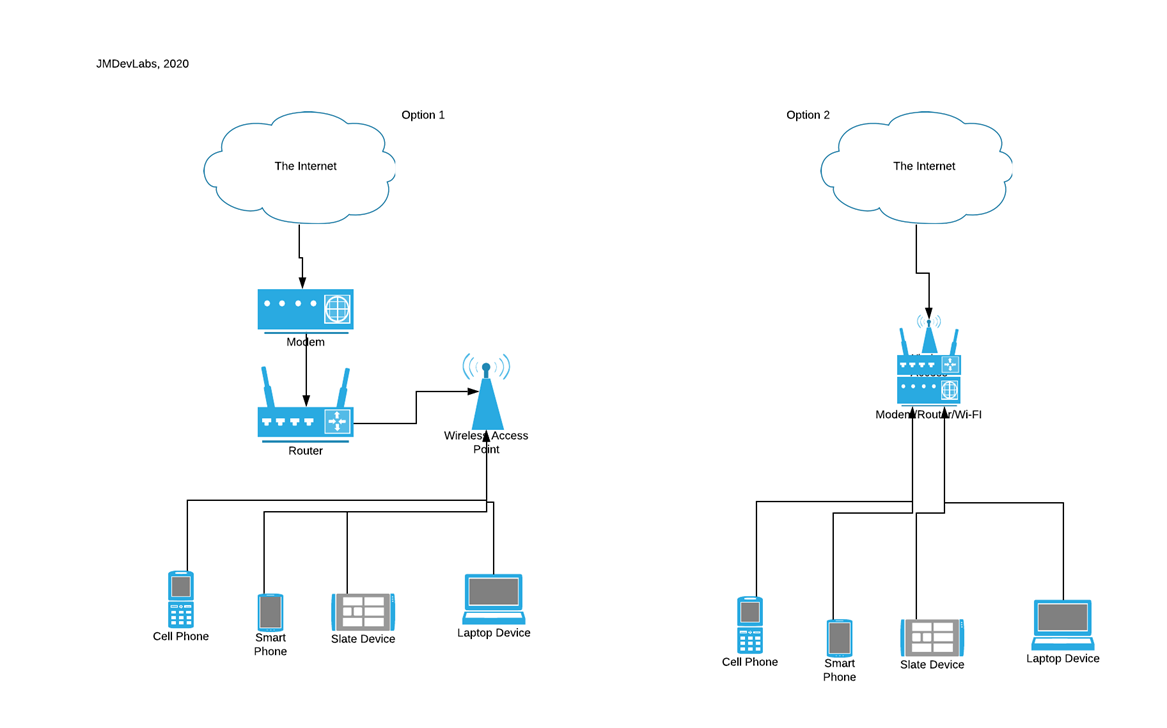
It is important to understand that in a network every device has a unique address. You might be wondering; how can that be possible if the internet provider only gives you ONE for your whole network? The answer is that, in either of the two options above, one of the devices is tasked with handing connected devices something called INTERNAL ADDRESSES. Those usually look something like 192.168.x.x. Here is a quick and easy way to check that using a terminal or command prompt, and simply typing ipconfig (ifconfig on non-window OS). The result should look something like this…
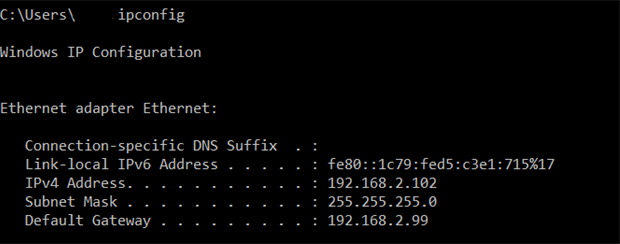
Kind of like your name, even with a first and last name, there will be others out there with identical names, however, your SSN is unique to each person. Inside your network, everyone gets an internal address, but all requests made to the internet will go out of your home network using the address given to your network by the internet providers. In the same way, when the responses from the internet return, they will come to the internet service address. That same device handing out internal addresses will translate from the external address to the internal one. This is like when you get mail at home, all mail comes to the same address, but the name on the package or envelope might let everyone know who it is for.
Ok, that was a lot of explanation, and we still have not gotten to the segmentation part. We are almost there, I promise.
Let’s go back to the internal network. If you run the command in the first caption and all the addresses have the same 3 numbers, then often those devices can see each other on the network. Its like houses on the same block, you can walk outside your hose and walk down the street and see all the neighbors’ houses. Take a look at the below caption…
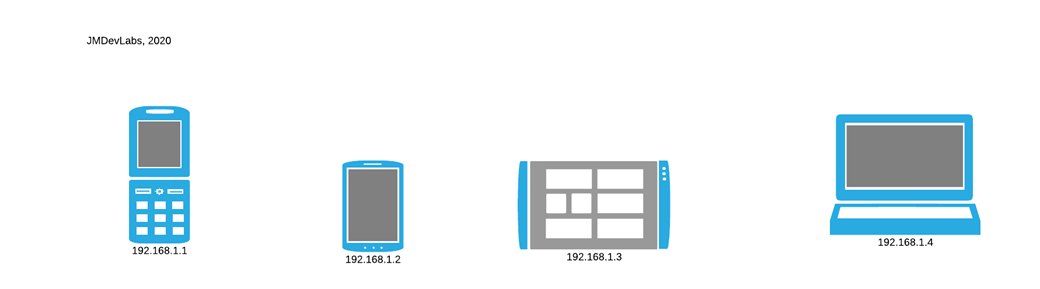
Why is this a problem?
Most of us have a home network full of simple devices that provide some measure of convenience, they do so by connecting themselves to the internet to allow us to interact with them remotely through an app or another connected device. Some of these include:
- Smart Thermostat
- Smart TV
- Smart coffee maker
- Smart washer and dryer
- Smart doorbell
- Smart cameras
- Smart vacuum
- Smart light fixtures
- Smart locks
- Alexa or Google Home
These are just some of the most popular ones. Some of these are mainstream enough that the developers have taken the time and have the resources to put their technologies to a rigorous testing cycle to discover possible vulnerabilities in the software. Others, not so much. As yourself, when was the last time your smart TV or smart light fixtures got a software update.
If all of these devices can communicate it increases the risk that a compromise smart device can be used as the gateway to infect other devices in your network like computers for example that might hold important personal information.
How does segmentation help fix the problem?
Finally, let us talk about how segmentation work. Segmentation allows you to create INTERNAL sub-networks and put some of the devices in there. Think of it as locking different members of the family in different rooms on the house and closing the door. They might all be able to see out the window and use the phone or tv, but they cannot see or talk to each other.
The same principle is applied to the network with segmentation, let us look at a graphical representation.
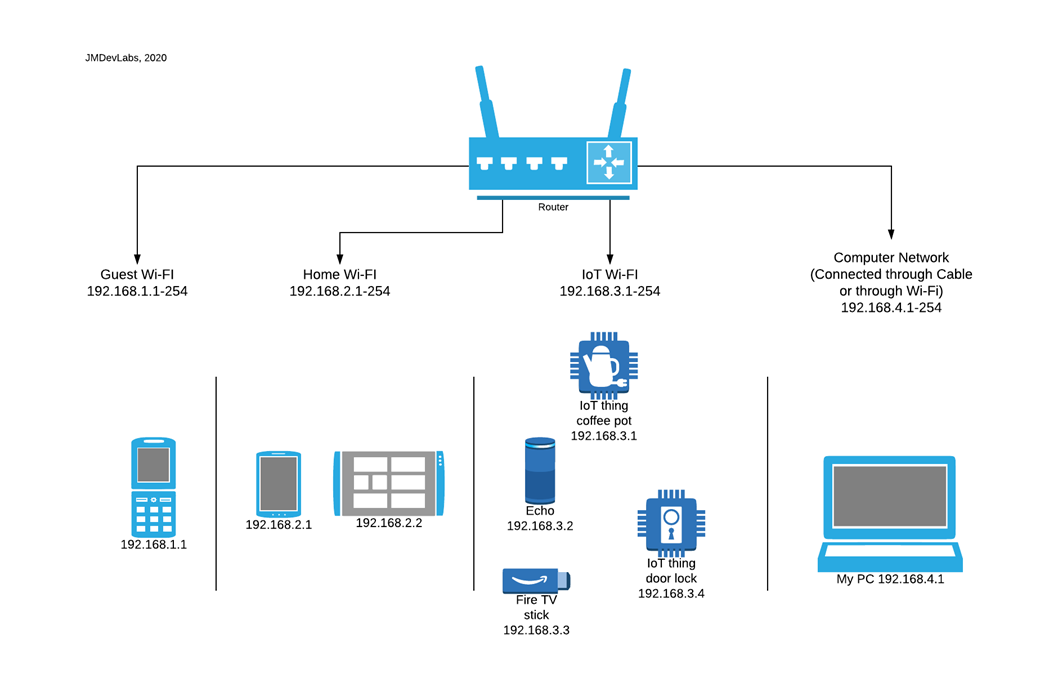
If you pay close attention to the above diagram, we can see that the 3RD number in each of the segments or subnets is different. What we have done here is put every type of device in a different room. All devices can connect to the internet as needed, but the IoT devices cannot connect to the mobile devices or computers, etc.
Consider this, when you invite your friends or relatives over to your place, do they clean their feet in the welcome mat as they enter, and often use the bathroom and wash their hands before having food? Would you be willing to put your friend’s hand in your mouth without asking them to wash it first? This is a particularly relevant question in recent times.
You should have the same mentality when it comes to other people’s devices, you don’t know where they have been. Why would you automatically assume that their devices are clean and allow them to come into your network where they can freely communicate with your devices.
Your friends are not bad people, after all, they are your friends. But how many cybersecurity friends do you have. Most people are very familiar with technology from a user perspective, but not so much from a security perspective. Your friend’s device could be compromised without him or her even knowing.
Computer viruses are a lot like real viruses (hence the name), they are looking for new hosts to spread.
Ok got it, segmentation helps, but how do I do it?
There are several ways to accomplish better network hygiene. Depending on what devices you already have in place it might be possible without much added cost. If you have a device at home that is older than 5 years old, not so much.
Before we look at options, let’s understand what we are trying to accomplish in order of importance.
- Separate Guest Wi-Fi from Home Wi-Fi
- Separate IoT devices from the rest of the home devices.
Ok, let us look at an average home router.
The RT-AC66R is a few years old now, but it is a popular device on Amazon and other retailers. Check the link below…
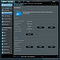
This device is certainly a capable one from a performance perspective, but it lacks some security features beyond basic segmentation. The RT-AC66R allows you to set up a GUESTS Wi-Fi networks, see below…
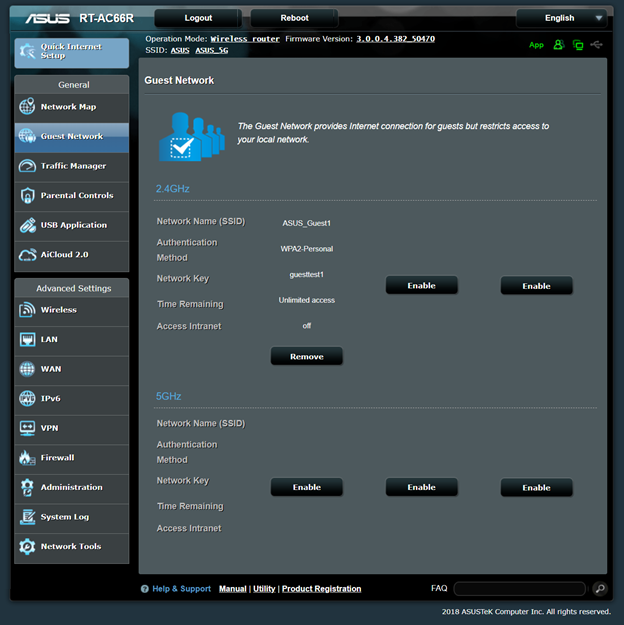
As outlined in the configuration portal, the guest networks can access the internet, but they cannot access other devices connected to the router using ethernet cables or the other Wi-Fi networks set up for the home users. This is a simplified version of segmentation, which uses something called private networks, or intra-network traffic blocking. Here the devices are still getting the same addresses, see below…
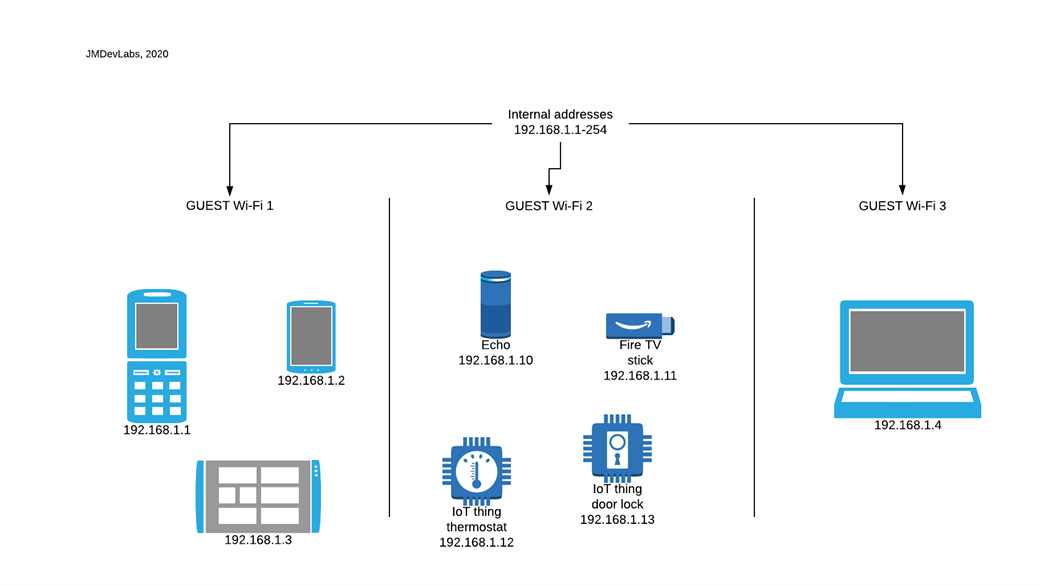
Devices are prevented from connecting to other devices in other segments. While this works, it is not ideal and does not provide much in the way of configuration for these guest networks. There is also another feature, SET AP ISOLATED, which also further restricts what each device can talk to within the same segment. See capture below…
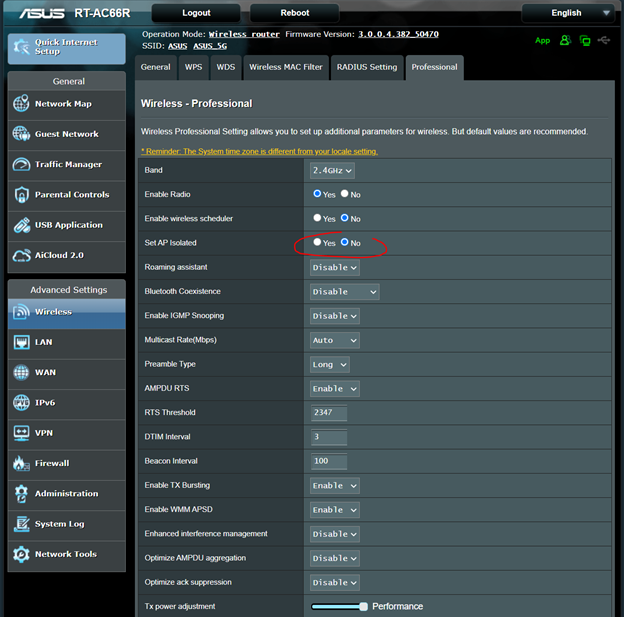
So here we are putting cubicles in the same room, we know we are not alone in the room, but we still cannot interact with the person in the next cubicle because the walls are too high.
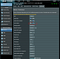
When both features are enabled you end up with something like this, see below…
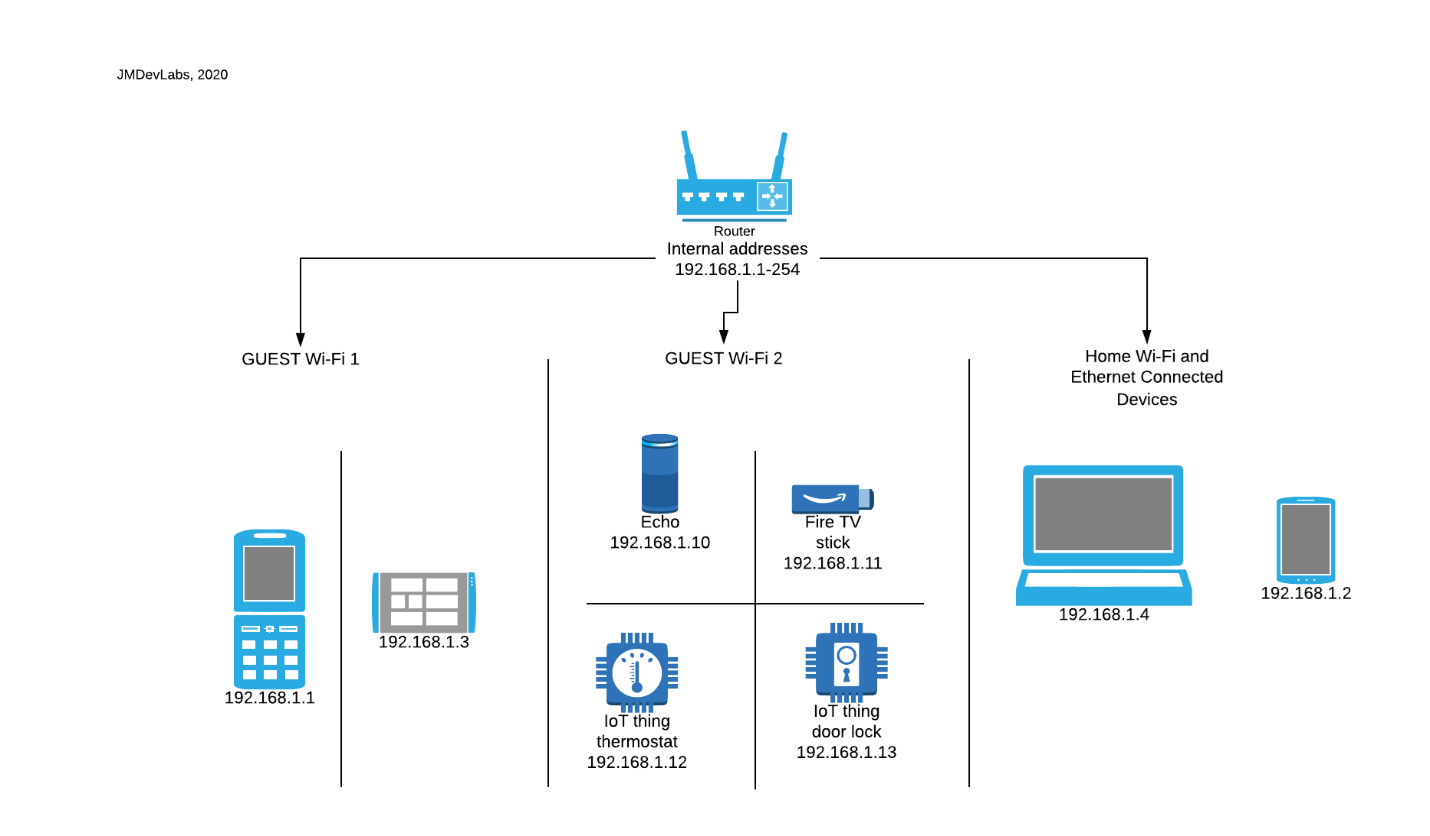
In the above graph, we can see that devices in GUEST Wi-Fi 1 cannot see each other, they also cannot see devices in GUEST Wi-Fi 2 or Home Wi-Fi & Ethernet Connected Devices. The same goes for Devices in GUEST Wi-Fi 2, they cannot see GUEST Wi-Fi 1 or the Home Network. The devices in the home network connected either through Wi-Fi or ethernet cable can all see each other.
Pretty good right? Well…
Yes, the above solution does provide separation of devices. But then there is not much in the way of configuration or flexibility. What happens if we have a smart device that connects through ethernet and not Wi-Fi, something like a TV, or a camera. That device now can see and communicate with both the laptop and the mobile device on the graph above.
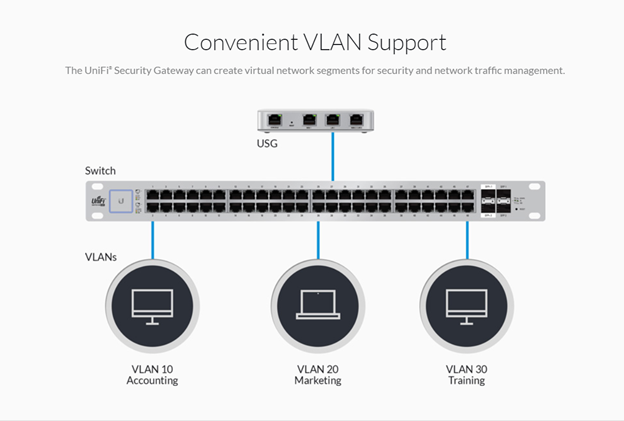
Some newer models allow better use of Virtual Networks or VLANs, a configuration feature that would allow you to divide the network logically and achieve better segmentation and would solve the problem presented in the previous paragraph. See one such model here…
Unfortunately, this model is more costly. Here is a link from the support page on how to configure the different VLANs on that router…

As you can see from one of the graphics, you can divide the internal interfaces into sub-networks with different address blocks (notice the 3rd group number is different). From what I can see in the management console photos, it looks like you can associate wireless SSIDs with Virtual Local Networks which means this solution solves problem 1 and 2, additionally if we had ethernet connected smart devices like a camera or smart TV we could separate it from other ethernet connected devices.
As mentioned before, this router is more expensive that the the RT-AC66R by quite a bit. Surprisingly, after much searching on the USA Asus site, it was the only one that clearly states as having the segmentation features that we want.
There are other solutions from multiple vendors with the ability to configure different network segments. Most of them are not routers, but rather switches or access points that can be connected to an existing router already in place in a home network.
Here are some options:
Ubiquiti (See the bought together section):
TP-Link (Combination of Access Point and Switch):
Access points:
https://amzn.to/2TbB22J, https://amzn.to/34duKpG
Switches:
https://amzn.to/37rJ5B0, https://amzn.to/35cvVoA ←this option offers Power Over Ethernet (POE) for access points that are sold without a power supply (yes, they are out there) because it is expected that the access point will draw its power from the switch. This is common for wall and ceiling mounted access points.
All of the above devices can be placed in your home network to achieve better network segmentation and thus preventing unwanted connections between potentially vulnerable devices which can lead to the spread of infection. Practice network distance! 😊
Lastly, it is remarkable how many vendors out there do not offer home network routers with the ability to segment the home network. Most routers from Asus, Netgear, and others seem to be focused on performance, gaming, and latency, not so much on security.
I hope that this article was helpful. I tried to simplify its content as much as possible in order to make it easier to understand and therefore some of the explanations are without a great deal of detail but rather an overview without too much tech mumbo-jumbo.
Enjoy!
J.







Comments
Post a Comment